
In 2021, there were 5.3 trillion computer intrusion attempts globally. Given that there are approximately 8 billion people on the planet, each person gets almost two unauthorized access attempts each day. Since malicious intrusion attempts are a form of cyberattack, Find the Firsts asks: What was the first recorded cyberattack?
Highlights:
- A cyberattack attempts to gain illegal access, via an electronic network, to a computer or computer system to cause damage or harm.
- The RABBITS program was the first computer virus in history.
- ARPANET, an experimental government computer network that was the Internet’s precursor, came to a crawl in 1980.
- In 1982, the CIA discovered a way to blow up a Siberian Gas pipeline using computer code.
- In 1988, an estimated 6,000 of the roughly 60,000 computers connected to the Internet were brought to a halt by a computer worm.
The definition of a cyberattack
Before uncovering the first cyberattack, we need to provide the meaning of the word “cyberattack.” According to Merriam-Webster’s dictionary, a cyberattack (also spelled cyber attack) is “an attempt to gain illegal access to a computer or computer system [to cause] damage or harm.” Here, we establish three components:
- The action is unauthorized or illegal.
- The target is a computer or multiple computers.
- The intent or result is malicious.
The National Institute of Standards and Technology goes one step further in its definition:
“An attack, via cyberspace, that targets an enterprise’s use of cyberspace to disrupt, disable, destroy, or maliciously control a computing environment/infrastructure; or destroying the integrity of the data, or steal controlled information.”
So, we add one more component to the definition of a cyberattack:
- The medium is cyberspace, the electronic world of computer networks.
While cyberspace can be any computer network, the Internet is a prominent example.
The debate over the first cyberattack
Several arguments exist for when the first recorded cyberattack occurred.
The French telegram system in 1834
Some sources quote the hacking of the French telegram system in 1834 as the first cyber attack. Two brothers who traded government bonds hijacked the government’s message relay system to gain faster updates on market movements, thus profiting from the information.
The telegram network consisted of towers with large, wooden arms at the top that an operator moved to relay a message. An operator at the first tower would start the message chain by setting the arm to a specific position. An operator at the next tower would use a telescope to see the configuration and place his arm accordingly. The process would repeat until the message reached its destination. According to our definition, since the buildings weren’t computers and the network wasn’t electronic, the hijacking wouldn’t qualify as the first cyberattack.
Later hacks also involved telephone systems.

The RABBITS Virus
There were examples of military code-breaking and life-saving computer hacks during World War II. Since these efforts weren’t malicious, they don’t qualify as cyberattacks.
The University of Washington saw the introduction of the first computer virus in history. In 1969, an unknown person installed a small program on one of the university’s computers. The program received the apt name of the RABBITS virus. The code made two copies of itself, and then each copy made two copies until the computer was overloaded and stopped working. Since the virus didn’t spread to other computers, it doesn’t meet the complete requirements (component #4) to define it as a cyberattack.
ARPANET crash of 1980
ARPANET (Advanced Research Projects Agency Network) was a government computer network that was the Internet’s precursor. On October 27, 1980, that network crashed, leaving it disconnected for four hours.
One of the devices, with a function similar to a router, had a hardware failure and was dropping bits. So, the nodes on the network produced different timestamps for the same message, and the process kept repeating. The “garbage collector” software couldn’t dispose of the status messages because the same message had multiple timestamps, and it didn’t know how to process that. The computers’ memory utilization then maxed out, bringing the system to a crawl. We refer to the behavior as a distributed denial of service (DDoS).
However, the crash wasn’t due to an actual human attack but a cascade of technical failures.
Captain “Zap”
In 1981, Ian Murphy, nicknamed “Captain Zap,” broke into the AT&T computer system and changed the internal clocks so the company would charge off-hour rates during peak times. The police arrested Murphy and convicted him of a felony. He paid a $1,000 fine, performed 1,000 hours of community service, and had two and a half years of probation. Later, Murphy served as a consultant for the movie “Sneakers.”
Since the incident involved physical entry and manual tampering, this doesn’t count as a cyberattack.
The original “Logic Bomb”
In 1982, with the Cold War in full swing, the Central Intelligence Agency of the United States (CIA) discovered a way to blow up a Siberian Gas pipeline without using a bomb or a missile. Calling it a “logic bomb,” the CIA inserted a code into equipment purchased by the Soviet Union from a company in Canada.
When the code eventually ran, the resulting explosion was so massive that the fire could be seen from space. Since the pipeline covered a remote area in Siberia, there were no reports of casualties.
Two factors rule this incident out as the first cyberattack. First, the CIA and the Russian government disavow the events occurring in the reported manner. Second, the code lived in the hardware and didn’t propagate throughout the system.
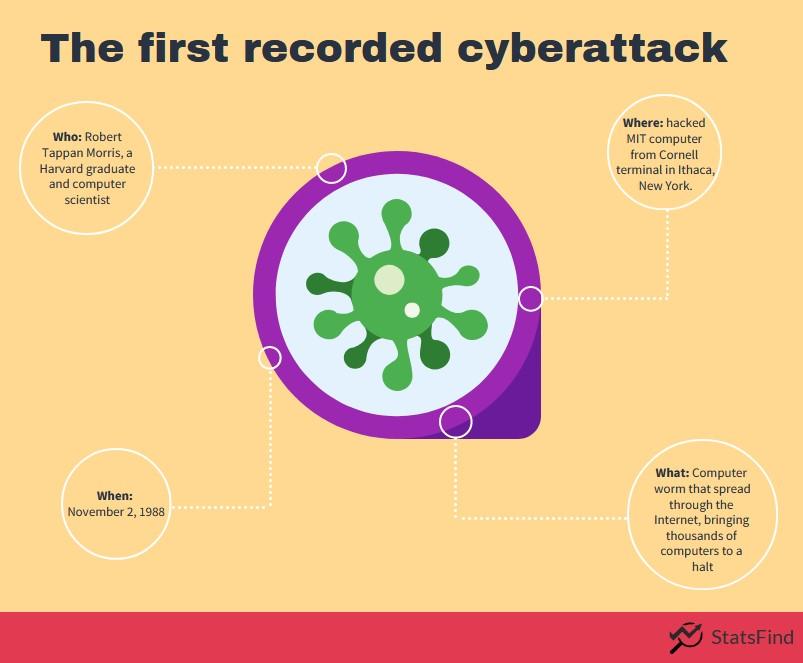
The first recorded cyberattack
Robert Tappan Morris, a Harvard graduate and talented computer scientist, started developing a program at Cornell University that could spread slowly and clandestinely across the Internet. On November 2, 1988, he released the code by hacking into an MIT computer from his Cornell terminal in Ithaca, New York.
Morris’ code had unintended consequences. His code was a computer worm, and computer worms, unlike viruses, don’t need a host but can exist and spread on their own. This cyber worm propagated at an incredible speed and brought computers to a halt. Within 24 hours, an estimated 6,000 of the roughly 60,000 computers connected to the fledgling Internet were affected. Some casualties were Harvard, Princeton, Stanford, Johns Hopkins, and NASA.
The actual damages were difficult to calculate, but estimates started at $100,000 and ascended into the millions.
Morris was the first person convicted of violating the 1986 Computer Fraud and Abuse Act. Morris didn’t go to jail, though. Instead, he received a fine, probation, and 400 hours of community service.
This event qualifies as the first recorded cyberattack. The action was unauthorized and illegal. The targets were multiple computers, the results were damaging, and the medium was cyberspace.
See more cyberattacks statistics.
Did you enjoy learning about the first recorded cyberattack?
Did you like these insights into the first recorded cyberattack? StatsFind regularly publishes articles from various fields, trending topics, and events throughout history that pique interest.
Want to learn more? Subscribe today!
More from StatsFind



Leave a Reply